
7 Must-Have Cloud Security Controls for Every Company
Security and privacy are hands down the biggest concerns when it comes to adoption of the cloud. For example, according to a recent ESG survey, more than half of the enterprises are still not comfortable storing regulated data in the cloud. Especially with recent revelations of Heartbleed, companies need to fully understand all of the risks associated with the cloud and set strict policies and controls to protect their regulated and critical business data.
I recently hosted the webinar “7 Must-Have Security Controls for Any Cloud Environment” with my colleague Varun Kohli. In this session, we shared a list of the seven must-have security controls for any cloud environment. In case you missed the webinar, here’s the list:#1 – Security Architecture: Consider the security of the entire stack delivering the service: from physical hardware and how that is secured, to virtual machines, the network (firewall rules, etc.), and all the way to the application.#2 – Identity and Access Management: It’s critical for a cloud solution to have a comprehensive identification and authorization framework. This framework is usually referred to as the 3 As of security – Authentication, Authorization and Access control. One of the popular requirements is for the cloud service provider (CSP) to support SAML and provide single sign-on capabilities. With the growing sophistication of hackers, having multi-factor authentication also reduces the risk of compromises to business data.#3 – Data Protection – Data protection addresses security across all aspects of the data lifecycle, starting from data creation all the way to how the CSP destroys it in case you move off of their service. The image below shows this lifecycle and the important security measures at each phase, with encryption being a key requirement throughout the cycle.
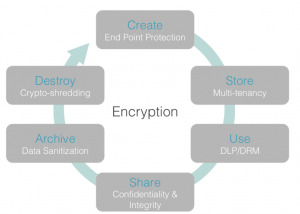
#4 – Governance: An organization relinquishes direct control over many aspects of security and data under the cloud paradigm, which makes governance key, as it provides visibility and control over policies, procedures, and standards for application development, implementation, and ongoing monitoring of deployed services in the cloud.#5 – Risk Management: CSPs must provide evidence of a robust risk assessment framework, which should include reports of vulnerability scans, static and dynamic application security testing and other risk assessment tools. Organizations of all sizes should take a hard look at what goes to the cloud and what does not. For example, some data and business files may be too sensitive to go into the cloud, such as PHI, PII, regulated data, intellectual property, mission critical content, etc.#6 – Compliance: Compliance is defined as conformance with an established specification, standard, regulation, or law. Your compliance requirements may be based on your industry, your company’s geographical location, or the location of the cloud data center your company uses. For example, some companies in Germany and certain financial organizations in Switzerland are required to keep European data in European data centers, which would cause those organizations to automatically rule out any CSP with data centers located in North America.In addition, with increased concerns around PRISM, MUSCULAR, and other government snooping programs, companies should obtain complete audit reports for all of its users, data and devices to stay on top of compliance at all times. #7 – Availability: When it comes to the consideration of a solution’s availability and uptime, most companies just look at the number of 9s in the SLA provided by their CSP. But, they often fail to consider about what happens when any of the following occurs:
- Temporary loss of access
- Outage – equipment/network failure
- Permanent loss of data
- Partial or complete
- Natural disaster
- Denial of Service
- Business continuity
- Disaster recovery
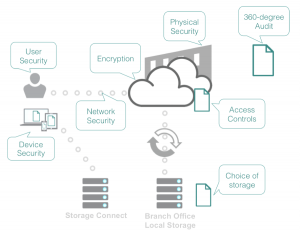
Egnyte bakes security right into the files’ lifecycle to ensure IT has full control over all corporate data, users and devices. The image below illustrates this lifecycle and various controls that Egnyte provides at different stages.
We hope this list of 7 must-have security controls will help you in choosing the right cloud solution to meet the needs of your organization. Want more information? Watch the webinar on-demand here.






